Facebook Updates as Malware
Facebook updates as malware
Recently, on my Android tablet, I started noticing these odd notifications about Facebook having downloaded an update, where it wanted me to click the notification to install it. This is a very odd paradigm on Android, and I was immediately concerned that it might be an attempt by a drive-by download to get malware installed onto my device. Maybe this is a good point to take a step back and explain a few things.
Android basics
Most Android devices ship with some sort of market pre-installed. Whether it’s the Play Store, or Amazon, this is the main place that most users find, download and install their apps. Generally, developers will publish their apps through these channels. One thing that these markets provide is a basic level of security against certain types of malware, and updates to apps that you already have installed, get handled in such a way that it would be almost difficult for you to go download a malware app pretending to be an update to an app that you have installed. There is usually a ‘my apps’ section in the market where you go download your updates, or where updates are autmatically managed for you. If an app wants to notify you of an update, they should pop a notification to take you to the Play Store, or the Amazon market, or perhaps Samsung’s app market depending on your configuration.
Multiple markets
Determining whether or not a specific market is present on a devices is actually trivially easy, and it should be just as easy to make reasonable guesses on how to fail back to less obvious markets if you find that the more popular ones are not installed.
Facebook’s strategy
Facebook’s new strategy seems to be that they should simply eschew the markets altogether and manage downloads themselves. I’ll take a stab at why they’re doing this, and why they might think it reasonable. Facebook, on the web, is famous for rolling out small experiments and A/B testing live on their site to see if a feature works, or how people will use it. This is really easy to do on the web. On mobile devices, you need to rely on your users updating their app regularly, and if you’re pushing out releases on a daily basis, it’s likely that your users will miss updates, and I would even venture to guess that a lot of users are just not real great about updating their apps on a regular basis. So, what’s happening on the Android app is that they have created their own pipeline for installations.
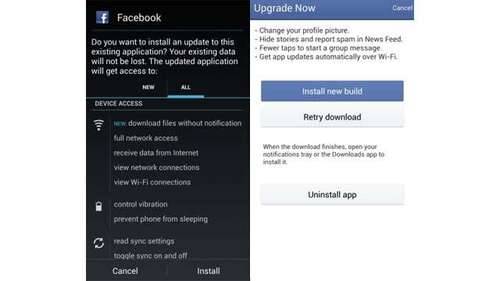
They notify you directly when there’s a new version, then when you click on the notification, you get a screen that asks you to download and install the update, or that they’ve already downloaded the app in the background, and it’s ready to install. They warn you that the version you are using has been depricated and are strongly pushing you to update. If you choose to update, you’ll be taken through the non-market package installation, which means that you have to have that setting enabled.
Android and malware
Something that many Android users may not be aware of is that malware is starting to become a real thing on Android. One vector of attack is something called the drive-by download. How it works is you visit a website that has been compramised, and you get an apk automatically downloaded to your device. The apk is named something like 'SecurityUpdate.apk’ or something that seems like you should install it. So, some users invariably do install it. It doesn’t seem like a huge problem right now, but it is a real thing, and companies like Lookout have been finding these attacks out in the wild. If you’re in the mood to do some research, I’d suggest Googling around for talks given by their engineers on Android security.
Why this is a dangerous stratgey
The basic problem with Facebook’s strategy is that it leverages the same drive-by download methods that malware does. What’s worse, is that these are real updates, users will start to get comfortable seeing updates being done like this, and as such, will be much more vulnerable to malware attacks going forward. Worse still, it would be trivially easy to copy Facebook’s design of their download/update page, and make it look like you’re going to download and install a Facebook update, when in reality, you’re actually downlaoding and installing malware.
Description of the attack
A Facebook specific attack would be fairly easy to do. First, create a web page that looks like the Facebook for Android update screen. Also, create a malware android app whose name is facebook_update.apk and the app icon is Facebook’s app icon. Then, do a drive-by download of that web page along with the malware app ( source ), and name it something like 'Click_to_download_Facebook_update.html’. This will show up in the user’s notification drawer as the title of the downloaded file, and some number of users will open it. Now, the user is presented with a familiar looking screen, where they can just click the install button like usual, and install the app. Now, just sit back and wait for the installs.
What to do
I am going to advise everyone I know to ignore those updates, and never install through that mechanism. If Facebook keeps pushing it, I’ll advocate for uninstalling the mobile app, and using the web version instead. I’ll also be sending an email to Facebook about this, and asking others to do the same. If you know an engineer at Facebook, even better. This is just completely irresponsible behavior on Facebook’s part, and they need to correct this.
PS - I wrote this, and the sample app from the car (driving from SF Bay to Reno for some weekend skiing), so please forgive any spelling or syntax errors.